"Is our data safe and secure?" is a question that is relevant not only as a regular consumer, but as a multi-unit operator. As operators and brands increasingly use software and technology to run their businesses, manage systems and procedures, and communicate crucial information across their organizations, data security also becomes more important.
When you trust technology vendors with your private company data, it's important to know that measures have been put in place to protect you, your stores, and your employees. Otherwise, the trickle-down effect of poorly managed data can ultimately lead to a poor customer experience and a loss of revenue.
Zenput is now SOC 2 Type II Certified
In order for customers and users of cloud-based software to feel confident and secure, providers can submit themselves to a third-party CPA firm that performs evaluations based on SOC 2 requirements. If the software company meets the stringent requirements over the course of the evaluation (typically six months to a year), they are awarded a certification that is not only hard to acquire, but one that demonstrates adequate controls are in place governing information security, and guarantees customers that their data is protected. So when you see a badge like the one below (which is also proudly displayed on Zenput's security page), you can rest assured that your data is in good hands. Zenput achieved this certification in late 2021.

So what is SOC 2?
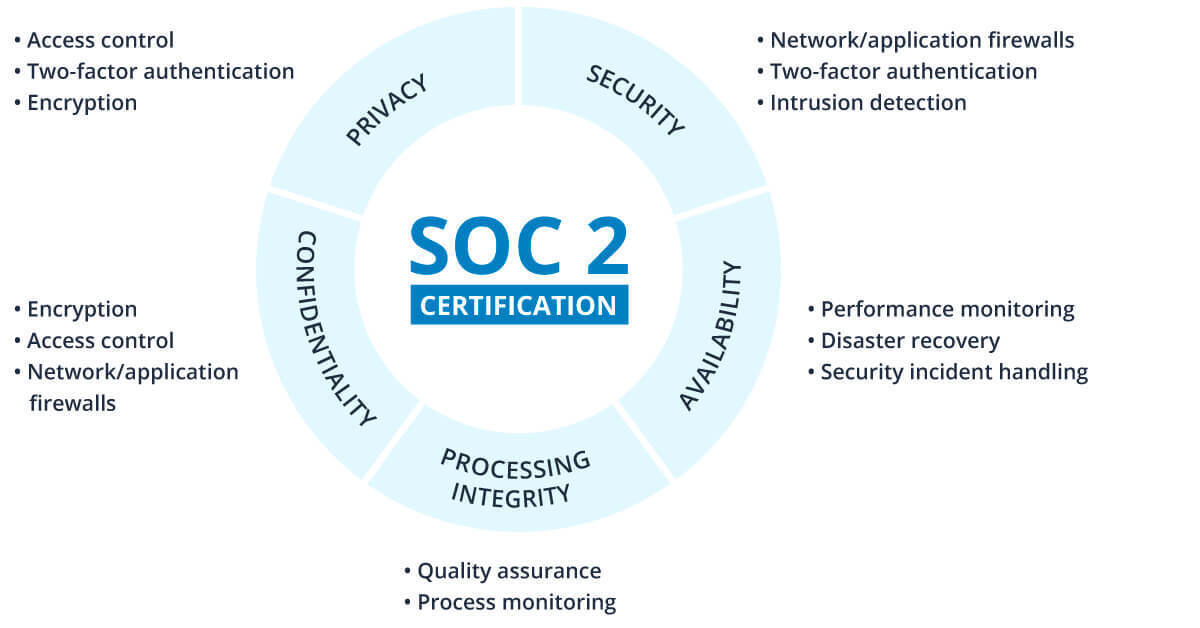
SOC stands for System Organization and Control, a framework created by the American Institute of Certified Public Accountants as a way to evaluate the adequate management of information. Service companies normally submit themselves to SOC 1, 2, or 3 depending on the nature and needs of the business. The audit reviews evidence related to the selected Trust Services Criteria (TSC) and is awarded to businesses after assessing their ability to comply with one or more of the following five trust principles:
Security
The Security Category has to do with the protection of information and requires that controls be put in place to protect against unauthorized access, unauthorized disclosure of information, and damage to systems that could compromise the availability. (the security category is required)
Availability
This principle refers to the accessibility of the system, products, services, and/or information.
Processing Integrity
Processing integrity focuses the completeness, validity, accuracy, timeliness, and authorization of system processing.
Confidentiality
The Confidentiality Category requires companies to demonstrate the ability to protect information throughout its lifecycle within the software.
Privacy
The Privacy Principle refers to the system's use of information throughout its lifecycle and includes protecting against the unauthorized access of personally identifiable information (PII).
Additionally, there are two types of SOC reports. Type I describes a vendor's systems and whether their design is suitable to meet relevant trust principles, and Type II details the operational effectiveness of those systems based on historical data that is collected over a period of time - usually a minimum of six months.
Why should restaurants, convenience stores, and retail operations care that the software they use is SOC 2 Compliant?
Whether you're sharing photos of issues or violations that need immediate attention, rolling out LTOs, new brand standards, or new policies, or dealing with corrective actions, you should never have to worry about data being leaked or seen by anyone harboring malicious intent. Like it or not, there is such thing as bad publicity, and in our time of instant communication, diligence is required to protect your brand and maintain the reputation you've worked so hard to establish.
So whether you're considering Zenput as your next software purchase to upgrade the way you operate, or if you're just truly curious about SOC 2 compliance, we hope this article was helpful.
But, if you want to learn more about the measures we've put in place to protect the data entrusted to us, please visit our security page.
Subscribe to our blog
You are now subscribed!